STORAGE MANAGEMENT
NETWORK MANAGEMENT
APPLICATION MANAGEMENT
SECURITY MANAGEMENT
SERVER PROVISIONING
SERVER MANAGEMENT
PROACTIVE MANAGEMENT, ALERTING & ESCALATION
Great features services
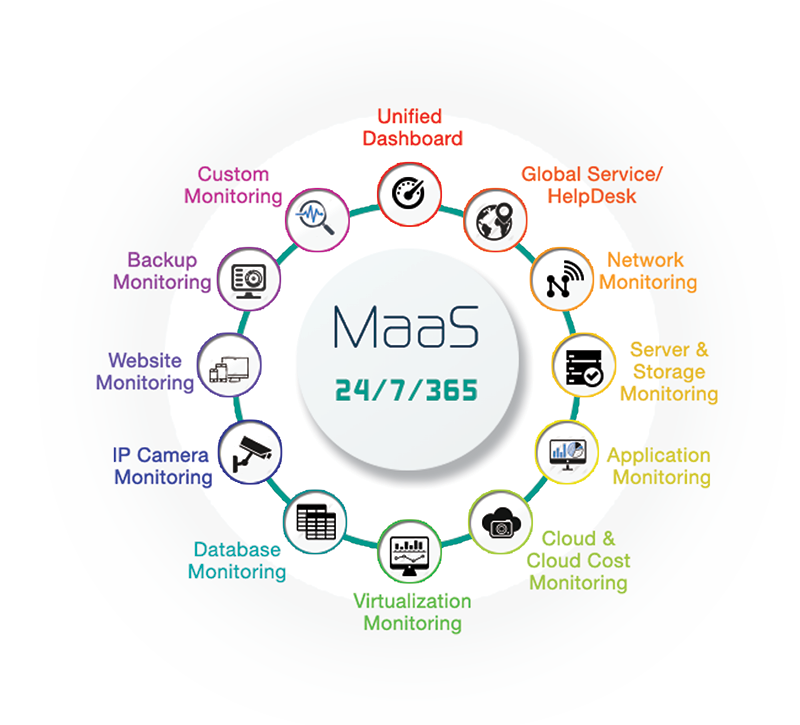
MONITORING AS A SERVICE (MAAS)
Scalability and Agility
Monitoring as a Service can support your business growth efficiently. “on demand” provisioning enables
our team to monitor or manage new cloud services or servers or network devices instantly.
Proactive
Get notified proactively by Email, SMS, Phone or mobile push notification before your servers, applications,
services, network devices or APIs go down.
No Infrastructure Costs
Our MaaS offering includes a team of 24×7 experts monitoring your services. Therefore, Customer does
not need to invest in an in-house IT team having that particular technology expertise.
Simplified Management
Our team deals with on-going management, maintenance and upgrades of technology. The customer can
focus on his core business needs.
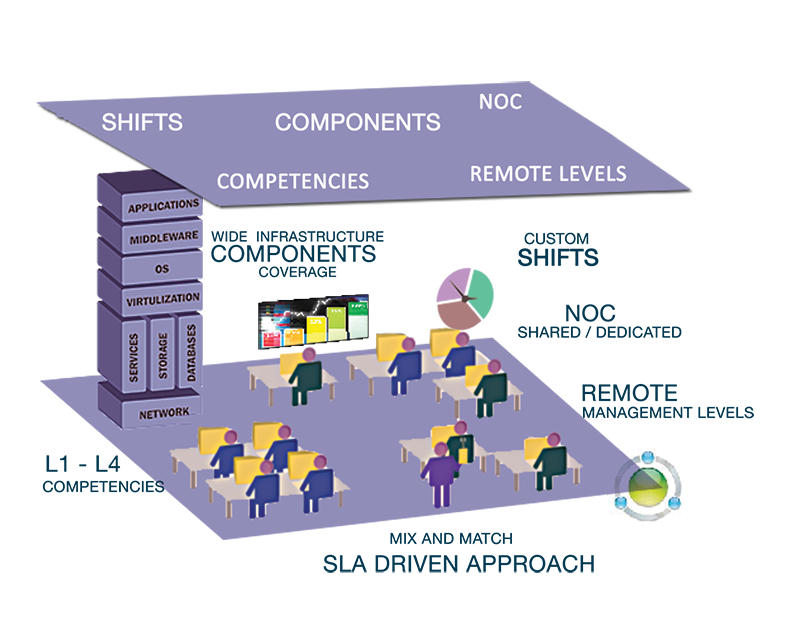
NOC AS A SERVICE
- mDesk Manage Dedicated or shared NOC with Level 1 – 4 technical Engineer’s.
- mDesk flexi provides customized NOC shifts.
- mDesk Managed Business continuity -24×7
- Managed data protection and Disaster Recovery NOC.
- mDesk 24×7 NOC service documents all emergency service calls.
- mDesk 24×7 NOC service provides monthly “Service review” meeting.
- mDesk 24×7 NOC has multiple channel of communication helpdesk tools, live support, phone, and email
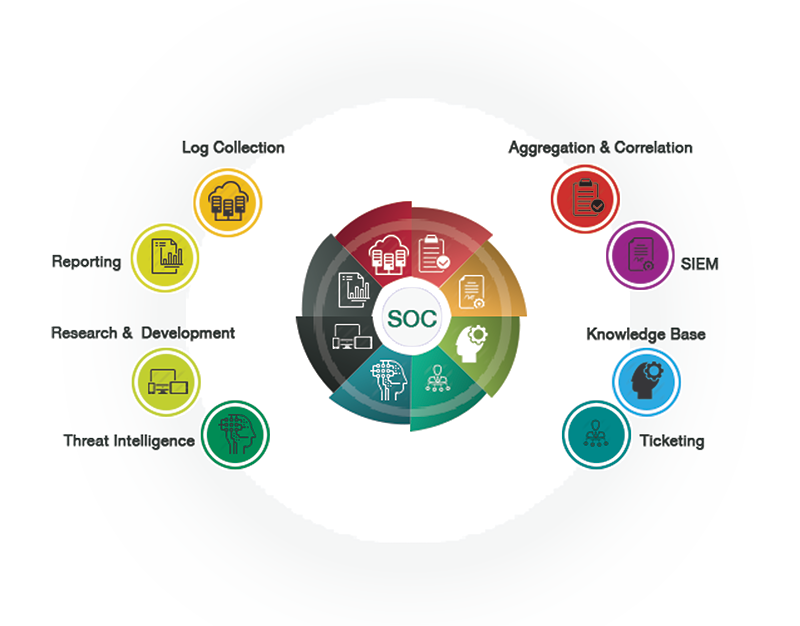
SOC AS A SERVICE
- Our Security Operations center services 24x7x365 combine threat intelligence, active security monitoring and advanced analytics to identify and responds to threats.
- Our Monitoring and Analytics services help to establish the cybersecurity capabilities on 24x7x365 with a proactive approach.
- Our Research, Investigations, Solutions and knowledge (RISK) cyber intelligence experts team will spot the threats before they do damage.
- SIEM platform configuration & Management.
- Advanced event correlation & anomalous user behavior detection.
- Remote threat & Alert validation.
- Regular threat briefings.
- Regulatory compliance reporting and Log Management.
- Continuous vulnerability scanning and reporting.
- Endpoint Security management & Penetration Testing.